This commit was a fix to `m_assumed_blockchain_size` reverted from
3fc2063's 220 to 9d0e528's 200 since work on 9d0e528 was being done in
parallel and ended up reverting `m_assumed_blockchain_size`.
This commits is now a intended to be a bump of
`m_assumed_blockchain_size` for both mainnet and testnet for new
reasonable values.
102faad81 Factor out combine / finalize / extract PSBT helpers (Glenn Willen)
78b9893d0 Remove op== on PSBTs; check compatibility in Merge (Glenn Willen)
bd0dbe876 Switch away from exceptions in refactored tx code (Glenn Willen)
c6c3d42a7 Move PSBT definitions and code to separate files (Glenn Willen)
81cd95884 Factor BroadcastTransaction out of sendrawtransaction (Glenn Willen)
c734aaa15 Split DecodePSBT into Base64 and Raw versions (Glenn Willen)
162ffefd2 Add pf_invalid arg to std::string DecodeBase{32,64} (Glenn Willen)
Pull request description:
* Move most PSBT definitions into psbt.h.
* Move most PSBT RPC utilities into psbt.{h,cpp}.
* Move wallet-touching PSBT RPC utilities (FillPSBT) into
wallet/psbtwallet.{h,cpp}.
* Switch exceptions from JSONRPCError() to new PSBTException class.
* Split DecodePSBT into DecodeBase64PSBT (old behavior) and DecodeRawPSBT.
* Add one new version of DecodeBase64 utility in strencodings.h (and
corresponding DecodeBase32 for completeness).
* Factor BroadcastTransaction utility function out of sendrawtransaction RPC
handler in rpc/rawtransaction.cpp
Note: For those keeping score at home wondering why refactor, this is in anticipation of (and developed in parallel with) a change to actually introduce GUI use of all this stuff, which is already under development and working-ish.
Tree-SHA512: 2197c448e657421f430943025357597e7b06c4c377d5d4b2622b9edea52a7193c48843dd731abb3a88ac4023a9c88d211991e0a9b740c22f2e1cbe72adefe390
318b1f7af1 [wallet] Close bdb when flushing wallet. (John Newbery)
Pull request description:
bdb would not be closed when closing the wallet in wallet-tool. Fix this by calling wallet->flush with true.
Tree-SHA512: f722e527e4806eca5254221e944f57853d11bf89a9264309fa558a6cc2b23feefb7bb2963e87b4fad9cfb31ac4cffe563688988e0614a481a8ff1d393aceb132
5039e4b61b Remove unnecessary const_cast (Julian Fleischer)
Pull request description:
The const_cast
```C++
CBlock &block = const_cast<CBlock&>(chainparams.GenesisBlock());
```
is not necessary as all the functions invoked form this block receive a `const CBlock&` anyway. Simply add the `const` to `block`:
```C++
const CBlock& block = chainparams.GenesisBlock();
```
Casting away `const`, especially from something as precious as the genesis block, feels really weird to me as a reader of bitcoin-core source code.
Tree-SHA512: 0290b2cabb216a60655ded153ed1f213c051fb216cec6f3f810f8b760e276f8def86eb696c492e89631682531e215f56d7897b59685d3aa787bcd80cc4f86c90
fa0ad4e7ce RPCHelpMan: Check default values are given at compile-time (MarcoFalke)
Pull request description:
Remove the run time assertions on the default values and ensure that the correct default type and value is provided at compile time.
Tree-SHA512: 80df2f3fab4379b500c773c27da63f22786c58be5963fe99744746320e43627a5d433eedf8b32209158df7805ebdce65ed4d242c829c4fe6e5d13deb4799ed42
1951ea434 gui: Show indeterminate progress dialog while opening walllet (João Barbosa)
8847cdaaa gui: Add OpenWalletActivity (João Barbosa)
4c8982a88 interfaces: Avoid interface instance if wallet is null (João Barbosa)
be82dea23 gui: Add thread to run background activity in WalletController (João Barbosa)
6c49a55b4 gui: Add Open Wallet menu (João Barbosa)
32a8c6abf gui: Add openWallet and getWalletsAvailableToOpen to WalletController (João Barbosa)
ab288b4e5 interfaces: Add loadWallet to Node (João Barbosa)
17abc0fd5 wallet: Factor out LoadWallet (João Barbosa)
Pull request description:
The *Open Wallet* menu has all the available wallets currently not loaded. The list of the available wallets comes from `listWalletDir`.
In the future the menu can be replaced by a custom dialog.
<img width="674" alt="screenshot 2019-01-12 at 12 17 02" src="https://user-images.githubusercontent.com/3534524/51073166-ac041480-1664-11e9-8302-be81702bc146.png">
Tree-SHA512: ebfd75eee0c8264863748899843afab67dadb7dff21313c11e3cb5b6108d954978dd1f1ae786bc07580c5a771ea4ab38d18c1643c9b9b3683ed53f0f6c582e38
a99999cc04 util: Add SetupHelpOptions() (MarcoFalke)
Pull request description:
Every binary we have sets up the help option in their own way and wording.
Solve that by having one function take care of it for all of them.
Tree-SHA512: 6e947fa8bc2a46fa6ca9f45777020aa269a5df0dd916ebc863224f9a1e0f79e8e7754a1478567307edd9461e8babd77d26bc2710bbd56e8f8da9020aa85a8c9c
Refactor the new CombinePSBT, FinalizePSBT, and FinalizeAndExtractPSBT
general-purpose functions out of the combinepsbt and finalizepsbt RPCs,
for use in the GUI code.
Remove the op== on PartiallySignedTransaction, which only checks that the
CTransactions are equal. Instead, check this directly in Merge, and return
false if the CTransactions are not equal (so the PSBTs cannot be merged.)
After refactoring general-purpose PSBT and transaction code out of RPC code,
for use in the GUI, it's no longer appropriate to throw exceptions. Instead we
now return bools for success, and take an output parameter for an error object.
We still use JSONRPCError() for the error objects, since only RPC callers
actually care about the error codes.
Move non-wallet PSBT code to src/psbt.{h,cpp}, and PSBT wallet code to
src/wallet/psbtwallet.{h,cpp}. This commit contains only code movement (and
adjustments to includes and Makefile.am.)
Factor out a new BroadcastTransaction function, performing the core work of the
sendrawtransaction rpc, so that it can be used from the GUI code. Move it from
src/rpc/ to src/node/.
Split up DecodePSBT, which both decodes base64 and then deserializes a
PartiallySignedTransaction, into two functions: DecodeBase64PSBT, which retains
the old behavior, and DecodeRawPSBT, which only performs the deserialization.
Add a test for base64 decoding failure.
Add support for the optional "pf_invalid" out parameter (which allows the caller
to detect decoding failures) to the std::string versions of DecodeBase32 and
DecodeBase64. The char* versions already have this feature.
Also, rename all uses of pfInvalid to pf_invalid to match style guidelines.
50e647210d Move ParseConfirmTarget from rpc/mining to rpc/util (Russell Yanofsky)
Pull request description:
Util is a better home since it's called both by wallet and mining code.
Suggested https://github.com/bitcoin/bitcoin/pull/15288#discussion_r254449444
Tree-SHA512: 4320caf2a3f70d2885c421de04f2ec68ff3f6519258c5155fc46e245dc1765fd15c81f260af5096318f24ff9deb88fc3c5ef40eec8b7393f467f5b963d17215b
30d0f7be6e rpc: Fix for segfault if combinepsbt called with empty inputs (benthecarman)
Pull request description:
Fixes#15300
Tree-SHA512: 25e7b4e6e48d8b0d197f0ab96df308fff33e2110f8929cb48914877fa7f4c4a84f173b1378fdb2dec5d03fe7d6d1aced4b577e55f9fe180d8147d9106ebf543f
7687f7873 [wallet] Support creating a blank wallet (Andrew Chow)
Pull request description:
Alternative (kind of) to #14938
This PR adds a `blank` parameter to the `createwallet` RPC to create a wallet that has no private keys initially. `sethdseed` can then be used to make a clean wallet with a custom seed. `encryptwallet` can also be used to make a wallet that is born encrypted.
Instead of changing the version number as done in #14938, a wallet flag is used to indicate that the wallet should be blank. This flag is set at creation, and then unset when the wallet is no longer blank. A wallet becomes non-blank when a HD seed is set or anything is imported. The main change to create a blank wallet is primarily taken from #14938.
Also with this, the term "blank wallet" is used instead of "empty wallet" to avoid confusion with wallets that have balance which would also be referred to as "empty".
This is built on top of #15225 in order to fix GUI issues.
Tree-SHA512: 824d685e11ac2259a26b5ece99c67a7bda94a570cd921472c464243ee356b7734595ad35cc439b34357135df041ed9cba951e6edac194935c3a55a1dc4fcbdea
A blank wallet is a wallet that has no keys, script or watch only things.
A new wallet flag indicating that it is blank will be set when the wallet
is blank. Once it is no longer blank (a seed has been generated, keys or
scripts imported, etc), the flag will be unset.
faa46475d7 wallet: Add lock annotation for mapAddressBook (MarcoFalke)
Pull request description:
This adds lock annotations for `mapAddressBook` and also moves one lock from inside `GetDestValues` to the caller to be in line with the other methods (`eraseDestData`, `addDestData`, ...)
Tree-SHA512: cef9397523e2f5717d4a9a6b2da1fe07042484a51b3c067ae64425768637f334350a2c3db4ab7e00af99b2a587f6b656b68ee1195f6a3db6d47298d0b2b6174a
eea02be70e Add locking annotation for vNodes. vNodes is guarded by cs_vNodes. (practicalswift)
Pull request description:
Add locking annotation for `vNodes`. `vNodes` is guarded by `cs_vNodes`.
Tree-SHA512: b1e18be22ba5b9dd153536380321b09b30a75a20575f975af9af94164f51982b32267ba0994e77c801513b59da05d923a974a9d2dfebdac48024c4bda98b53af
1cff3d6cb0 Change in transaction pull scheduling to prevent InvBlock-related attacks (Gleb Naumenko)
Pull request description:
This code makes executing two particular (and potentially other) attacks harder.
### InvBlock
This behavior was described well [here](https://www.cs.umd.edu/projects/coinscope/coinscope.pdf) (page 11).
Per current implementation, if node A receives _INV_ (tx) from node B, node A sends _GETDATA_ to B and waits for _TX_ message back.
Node A is likely to receive more _INVs_ (regarding the same tx) from other peers. But node A would not send another _GETDATA_ unless it does not hear _TX_ back from node B for next 2 minutes (to save bandwidth)
Thus, if B is a malicious node, it can prevent node A from getting the transaction (even if all A’s peers have it) for 2 minutes.
This behavior seems to be an inherent limitation of the current P2P relay protocol, and I don’t see how it can be fundamentally changed (I can see workarounds which involve rewriting a lot of P2P code though).
### What does this PR fix?
The attacks I’m looking at involve preventing A from learning the transaction for 2*N minutes. To do that, an attacker has to spin up N nodes and send N _INVs_ simultaneously to node A (then InvBlocks will be queued with an interval of 2 minutes according to current implementation)
More precisely, 2 scenarios I’m looking at are:
1. An attacker censors a particular transaction. By performing InvBlock from different nodes, an attacker can execute a network-wide censorship of a particular transaction (or all transactions). The earlier an attacker founds the transaction he wants to censor, the easier it is to perform an attack. As it was pointed out by @gwillen, this is even more dangerous in the case of lightning, where transactions are known in advance.
2. Topology inference described in papers [1](https://www.cs.umd.edu/projects/coinscope/coinscope.pdf), [2](https://arxiv.org/pdf/1812.00942.pdf) involve network-wide InvBlock. This fix would not mitigate this type of inference, but I believe it will make it more expensive to perform (an attacker would have to create more transactions and perform more rounds to learn the topology, the second paper itself notes that InvBlock isolation is important for the attack).
### How does it work
This PR introduces bias toward outbound connections (they have higher priority when a node chooses from whom it should request a transaction) and randomizes the order.
As per @gmaxwell suggestion, GETDATA requests queue is created after processing all incoming messages from all nodes.
After this fix, if the incoming messages were [I1, I2, I3, O1, O2, O3, O4], the queue for _GETDATA_ may look like [O2, O1, O3, O4, I1, I3, I2, ….].
If {I1, I2, I3} were significantly earlier (but the difference is less than TX_TIMEOUT=60 s) than others, the queue for _GETDATA_ may look like [I2, O2, O1, O3, O4, I1, I3, ….].
### Other comments:
1. This mitigation works better if the connectivity is higher (especially outbound, because it would be less likely that 2 _GETDATAs_ for inbound malicious nodes queued together)
Tree-SHA512: 2ad1e80c3c7e16ff0f2d1160aa7d9a5eaae88baa88467f156b987fe2a387f767a41e11507d7f99ea02ab75e89ab93b6a278d138cb1054f1aaa2df336e9b2ca6a
b985e9c850 Add release notes for importmulti descriptor support (MeshCollider)
fbb5e935ea Add test for importing via descriptor (MeshCollider)
9f48053d8f [wallet] Allow descriptor imports with importmulti (MeshCollider)
d2b381cc91 [wallet] Refactor ProcessImport() to call ProcessImportLegacy() (John Newbery)
4cac0ddd25 [wallet] Add ProcessImportLegacy() (John Newbery)
a1b25e12a5 [wallet] Refactor ProcessImport() (John Newbery)
Pull request description:
~~Based on #14454#14565, last two commits only are for review.~~
Best reviewed with `?w=1`
Allows a descriptor to be imported into the wallet using `importmulti` RPC. Start and end of range can be specified for ranged descriptors. The descriptor is implicitly converted to old structures on import.
Also adds a simple test of a P2SH-P2WPKH address being imported as a descriptor. More tests to come, as well as release notes.
Tree-SHA512: 160eb6fd574c4ae5b70e0109f7e5ccc95d9309138603408a1114ceb3c558065409c0d7afb66926bc8e1743c365a3b300c5f944ff18b2451acc0514fbeca1f2b3
595283851 [rpc] util: add deriveaddresses method (Sjors Provoost)
Pull request description:
Usage:
```sh
bitcoin-cli deriveaddresses "wpkh([d34db33f/84h/0h/0h]xpub6DJ2dNUysrn5Vt36jH2KLBT2i1auw1tTSSomg8PhqNiUtx8QX2SvC9nrHu81fT41fvDUnhMjEzQgXnQjKEu3oaqMSzhSrHMxyyoEAmUHQbY/0/0)"
[
"bc1qg6ucjz7kgdedam7v5yarecy54uqw82yym06z3q"
] // part of the BIP32 test vector
```
Avoids the need for external (BIP32) libraries to derive an address. Can be used in conjunction with `scantxoutset` as a poor mans wallet. Might be useful to test more complicated future descriptors.
~To keep it as simple as possible it only supports descriptors that result in a single address, so no `combo()` and ranges.~
As discussed recently on IRC it might make sense to put this in a separate utility along with other descriptor and psbt utility functions which don't need a chain or wallet context. However I prefer to leave that to another PR.
Tree-SHA512: b8e53db11a8fd87638cc98766270cc3be9adc4b3e5085798a6a4e2e6ad252bf6d2189346bbb2da72d04d13f7f1e80b5cb88e8039653bea1f150602a876ef7f34
87aa0b48af netaddress: Make IPv4 loopback comment more descriptive (Carl Dong)
6180b5f32b netaddress: Fix indentation in IsLocal (Carl Dong)
Pull request description:
This also makes the comment match the IPv6 comment just below this hunk.
Tree-SHA512: 9b91195e71e18156c9e013f63a6d430c67951aabb4a0c2f48f3bf852570c13887572b9e2fa52f4e1beba8685a9cae8949d4d03cd618a78f88566cf9e85dc64a8
fa2a69fcb9 doc: Add cs_main lock annotations for mapBlockIndex (practicalswift)
Pull request description:
Marked as "doc" because it didn't change the bitcoind on my system with default configure settings for both gcc and clang.
Tree-SHA512: ba203f16c1cdc834a61c65bb5fb20bbaf7d8bff0c3a1b8ef46bc1d3669092191221e26abd7e580efab2f9bd5a992dc363251f1b68c6cd68f8204d62675868cf1
e8db6b8044 Qt: Fix update headers-count (Jonas Schnelli)
7bb45e4b7a Qt: update header count regardless of update delay (Jonas Schnelli)
Pull request description:
Update the block and header tip is constraint to have a minimal distance of 250ms between updates... which can lead to miss the last header update.
The modal overlay then assumes we are still in header sync and the view get stuck in "syncing headers,..." (while it's actually syncing blocks).
This removes the 250ms minimal delta for header updates as well as it fixes the correct display of how header updates should update the labels.
Tree-SHA512: 57608dac822b135cd604fc6ba1c80f25c0202a6e20bb140362026615d4bf243ef4fcc254a11bad36419c554a222a2f4947438d4ce44aa14041d1874751643d68
47012391ec [Docs] Small updates to getrawtransaction description (Amiti Uttarwar)
Pull request description:
As per review comments on https://github.com/bitcoin/bitcoin/pull/15159
Tree-SHA512: 0bbbe956b47d177f7e67c5ab2048287783327d9e07a679d64d79aee3ea8633e769f75b59d3dbce517924ba5d64d6c44f26bf49e16d40612463e460ad1a238129
ef0b01217a tests: Make updatecoins_simulation_test deterministic (practicalswift)
Pull request description:
Make test `updatecoins_simulation_test` deterministic.
Can be verified using `contrib/test_deterministic_coverage.sh` introduced in #15296.
Related:
* #15296: "tests: Add script checking for deterministic line coverage in unit tests"
* #15324: "test: Make bloom tests deterministic"
* #14343: "coverage reports non-deterministic"
Tree-SHA512: 3466e28a42dd3735effb8542044d88e8350a470729d4a4f02abce9d6367de6568d698131469ba154d3dc76d448bacb360b7aefd066bb5b91408c0be375dd3ecb
364cff1cab Fix issue #9683 "gui, wallet: random abort (segmentation fault) running master/HEAD". (Chris Moore)
Pull request description:
Patch taken from @ryanofsky's comment https://github.com/bitcoin/bitcoin/issues/9683#issuecomment-448035913.
[MarcoFalke wrote](https://github.com/bitcoin/bitcoin/issues/9683#issuecomment-454066004):
> Mind to submit this patch as a pull request?
So that's what I'm doing.
I was regularly seeing crashes on startup before applying this patch and haven't seen a single crash on startup since applying it almost a month ago.
Tree-SHA512: 3bbb2291cdf03ab7e7b5b796df68d76272491e35d473a89f4550065554c092f867659a7b8d7a1a91461ae4dc9a3b13b72541eafdbd732536463e9f3cf82300c8
0164b0f5cf build: Remove WINVER pre define in Makefile.leveldb.inlcude (Chun Kuan Lee)
d0522ec94e Drop defunct Windows compat fixes (Ben Woosley)
d8a2992067 windows: Call SetProcessDEPPolicy directly (Chun Kuan Lee)
1bd9ffdd44 windows: Set _WIN32_WINNT to 0x0601 (Windows 7) (Chun Kuan Lee)
Pull request description:
The current minimum support Windows version is Vista. So set it to 0x0600
5a88def8ad/mingw-w64-headers/include/sdkddkver.h (L19)
Tree-SHA512: 38e2afc79426ae547131c8ad3db2e0a7f54a95512f341cfa0c06e4b2fe79521ae67d2795ef96b0192e683e4f1ba6183c010d7b4b8d6b3e68b9bf48c374c59e7d
851380ce17 remove deprecated mentions of signrawtransaction from fundraw help (Gregory Sanders)
Pull request description:
RPC call has been removed as of 0.17.99.
Tree-SHA512: a6a12a0e4572acd9b532c1719be85ed6f29d1c1a28f9ce691398528b8dde4fb4a3222b8f68632fcb1a8eddfe2d31e96d5efd5bc51c041af8e7cb99b61ca3a167
aebafd0edf Rename Chain getLocator -> getTipLocator (Russell Yanofsky)
2c1fbaa771 Drop redundant get_value_or (Russell Yanofsky)
84adb206fc Fix ScanForWalletTransactions start_block comment (Russell Yanofsky)
2efa66b464 Document rescanblockchain returned stop_height being null (Russell Yanofsky)
db2d093233 Add suggested rescanblockchain comments (Russell Yanofsky)
a8d645c934 Update ScanForWalletTransactions result comment (Russell Yanofsky)
95a812b599 Rename ScanResult stop_block field (Russell Yanofsky)
Pull request description:
This implements suggested changes from #14711 review comments that didn't make make it in before merging.
There are no changes in behavior in this PR, just documentation updates, simplifications, and variable renames.
Tree-SHA512: 39f1a5718195732b70b5e427c3b3e4295ea5af6328a5991763a422051212dfb95383186db0c0504ce2c2782fb61998dfd2fe9851645b7cb4e75d849049483cc8
This commit adds a ProcessImportLegacy() function which
currently does nothing. It also unindents a block of
code for a future move-only change.
Reviewer hint: review with -w to ignore whitespace changes.
This commit is move-only and doesn't make any functional changes. It
simply moves code around within ProcessImport() in preparation for
refactors in the next commits.
77777c5624 log: Construct global logger on first use (MarcoFalke)
Pull request description:
The (de)initialization order is not well defined in C++, so generally it is not safe to use globals as the (de/con)structor of one global could use the (de/con)structor of another global before/after it has been (con/de)structed.
Specifically this fixes:
* `g_logger` might not be initialized on the first use, so do that. (Fixes#15111)
Tree-SHA512: eb9c22f4baf31ebc5b0b9ee6a51d1354bae1f0df186cc0ce818b4483c7b5a7f90268d2b549ee96b4c57f8ef36ab239dc6497f74f3e2ef166038f7437c368297d
- Update transifex slug
- Mention update of MSVC build in `doc/translation_process.md`
- Do a `make translate` to update English translations
- Pull current translations from transifex
712d35bc56 wallet: Add missing cs_db lock (João Barbosa)
Pull request description:
Without this lock `BerkeleyEnvironment::~BerkeleyEnvironment` and `GetWalletEnv` would race for `g_dbenvs`. This wasn't detected before because thread safety analysis does not check constructors
and destructors.
Reference: http://releases.llvm.org/5.0.2/tools/clang/docs/ThreadSafetyAnalysis.html#no-checking-inside-constructors-and-destructors
Tree-SHA512: 350cb2b991ca699a6bca85f87c82c38f0814484c8ccb0d7d83cb3bff9afcf60dd32b2a9554a9e72eb5803bfad8b6970fe7da618b39be5889178b86faa1b74124
fae169c95e test: Make bloom tests deterministic (MarcoFalke)
Pull request description:
non-deterministic tests are useless, since a failing test could not be reproduced unless the seed is known.
Tree-SHA512: 4f634ff0c6adf663444f1ac504f6dbceaa46b78d697b840531977ba30006453ac559d5c21cc3eaef6d92b87d46008a34b0db6331ea3318001987fcfaec634acf
This introduces support for autodetecting and using the RdSeed instruction.
In addition:
* In SeedFast, only 64 bits of entropy are generated through RdRand (256 was relatively slow).
* In SeedStartup, 256 bits of entropy are generated, using RdSeed (preferably) or RdRand (otherwise).
When a wallet is created it is registered in the validation interface (in
CWallet::CreateWalletFromFile) but it is not immediately added to the
wallets list. If a shutdown is requested before AddWallet (case more
evident when -rescan is set) then m_internals can be released (in
Shutdown -> UnregisterBackgroundSignalScheduler) before the wallet and
then ReleaseWallet would call UnregisterValidationInterface with
m_internals already released.
This change forwards the shutdown request on the GUI (close the
application for instace) to the node as soon as possible. This way the
GUI doesn't have to wait for long operations to complete (rescan the
wallet for instance), instead those operations detect the shutdown
request and abort/interrupt.
Move only change that makes unsubscribeFromCoreSignals public. It must be
called if the event loop is not running otherwise core signals handlers
can deadlock.
11e0fd8d6 Descriptor expansions only need pubkey entries for PKH/WPKH (Pieter Wuille)
Pull request description:
Currently, calling `Expand` on a `Descriptor` object will populate the output FlatSigningProvider with all public keys involved in the descriptor. This is overkill, as pubkey entries are only needed when the lookup of a public key based on its hash is desired (which is the case for `pkh`, `wpkh`, and `combo` descriptors).
Fix this by pushing the population of pubkey entries down into the individual descriptor implementation's `MakeScript` function, instead of doing it generically.
This should make it easier to implement #14491 without importing P2PKH outputs for the individual public keys listed inside a multisig.
Tree-SHA512: 5bc7e9bd29f1b3bc63514803e9489b3bf126bfc177d46313aa9eeb98770ec61a97b55bd8ad4e2384154799f24b1bc4183bfdb4708b2ffa6e37ed2601a451cabc
Without this lock BerkeleyEnvironment::~BerkeleyEnvironment and
GetWalletEnv would race for g_dbenvs. This wasn't detected before
because thread safety analysis does not check constructors and
destructors.
119d360aab travis: Document whether functional tests are run in the job name (Ben Woosley)
64f28545e3 Revert "travis: Compile trusty with depends for now" (Ben Woosley)
267eac00f9 Prefer boost::optional#get_value_or over #value_or (Ben Woosley)
1971f5ba04 Piecewise construct to avoid invalid construction (Ben Woosley)
Pull request description:
In light of #14979, I realized that only qt 5.5+ was being tested under CI, while compatibility lists 5.2+.
In #15276, Marco added Trusty to CI, building with depends. This changes that build to system libraries, in order to ensure ongoing compatibility with our claimed minimum required versions.
Fixes#14983, previously open as #14998
Tree-SHA512: 6cff5e28c756ecb8bf797c8f6eb77c1944ba61a8dd6d7d4984e63eef384f6429dc79c505da3241c05b9c4db31c72b2a9846c7365aba9280f2e0620e5f3998d07
e6c58d3b01 Do not import private keys to wallets with private keys disabled (Andrew Chow)
b5c5021b64 Refactor importwallet to extract data from the file and then import (Andrew Chow)
1f77f6754c tests: unify RPC argument to cli argument conversion and handle dicts and lists (Andrew Chow)
Pull request description:
Fixes a bug where private keys could be imported to wallets with private keys disabled. Now every RPC which can import private keys checks for whether the wallet has private keys are disabled and errors if it is. Also added an belt-and-suspenders check to `AddKeyPubkeyWithDB` to have it assert that the wallet has private keys enabled.
Tree-SHA512: 5cd04febce9aa2bd9bfd02f312c6ff8705e37278cae59efd3895f6d6e2f1b477aefd297e2dd0860791bdd3d4f3cad8eb1a404f8f3d4e2035b91314ad2c1028ae
In CMainSignals::RegisterWithMempoolSignals running under Ubuntu 14.04
(QT 5.2), absent piecewise construction this fails to create the pair
because the argument is a connection, which is converted into a
non-copyable scoped_connection.
validationinterface.cpp:80:186: required from here
/usr/include/boost/signals2/connection.hpp:234:7: error: ‘boost::signals2::scoped_connection::scoped_connection(const boost::signals2::scoped_connection&)’ is private
scoped_connection(const scoped_connection &other);
^
In file included from /usr/include/c++/4.8/utility:70:0,
from /usr/include/c++/4.8/algorithm:60,
from ./prevector.h:13,
from ./script/script.h:10,
from ./primitives/transaction.h:11,
from ./validationinterface.h:9,
from validationinterface.cpp:6:
/usr/include/c++/4.8/bits/stl_pair.h:134:45: error: within this context
: first(std::forward<_U1>(__x)), second(__y) { }
https://travis-ci.org/bitcoin/bitcoin/jobs/473689141#L2172
14bc2a17dd Trivial: add doxygen-compatible comments relating to BerkeleyEnvironment (Pierre Rochard)
88b1d956fe Tests: add unit tests for GetWalletEnv (Pierre Rochard)
f1f4bb7345 Free BerkeleyEnvironment instances when not in use (Russell Yanofsky)
Pull request description:
Instead of adding BerkeleyEnvironment objects permanently to the g_dbenvs map, use reference counted shared pointers and remove map entries when the last BerkeleyEnvironment reference goes out of scope.
This change was requested by @TheBlueMatt and makes code that sets up mock databases cleaner. The mock database environment will now go out of scope and be reset on destruction so there is no need to call BerkeleyEnvironment::Reset() during wallet construction to clear out prior state.
This change does affect bitcoin behavior slightly. On startup, instead of same wallet environments staying open throughout VerifyWallets() and OpenWallets() calls, VerifyWallets() will open and close an environment once for each wallet, and OpenWallets() will create its own environment(s) later.
Tree-SHA512: 219d77a9e2268298435b86088f998795e059fdab1d2050ba284a9ab8d8a44961c9b5cf96e94ee521688108d23c6db680e3e3a999b8cb2ac2a8590f691d50668b
3c3e31c3a4 [tests] Add wallet-tool test (João Barbosa)
49d2374acf [tools] Add wallet inspection and modification tool (Jonas Schnelli)
Pull request description:
Adds an offline tool `bitcoin-wallet-tool` for wallet creation and maintenance.
Currently this tool can create a new wallet file, display information on an existing wallet, and run the salvage and zapwallettxes maintenance tasks on an existing wallet. It can later be extended to support other common wallet maintenance tasks.
Doing wallet maintenance tasks in an offline tool makes much more sense (and is potentially safer) than having to spin up a full node.
Tree-SHA512: 75a28b8a58858d9d76c7532db40eacdefc5714ea5aab536fb1dc9756e2f7d750d69d68d59c50a68e633ce38fb5b8c3e3d4880db30fe01561e07ce58d42bceb2b
2bc4c3eaf9 Notify the GUI that the keypool has changed to set the receive button (Andrew Chow)
14bcdbe09c Check for more than private keys disabled to show receive button (Andrew Chow)
Pull request description:
Currently the Receive button in the GUI is displayed enabled or disabled by the initial state of the wallet when the wallet is first loaded. The button is only enabled or disabled depending on whether the disable private keys flag is set when the wallet is loaded. However, future changes to the wallet means that this initial state and check may no longer be accurate. #14938 introduces empty wallets which do not have private keys. An empty wallet that is loaded should have the Receive button disabled, and then it should become enabled once `sethdseed` is used so that a keypool can be generated and new keys generated. Likewise, with #14075, a wallet can be loaded with no keypool initially, so the button should be disabled. Later, public keys can be imported into the keypool, at which time the button should become enabled. When the keypool runs out again (no new keys are generated as the keypool only consists of imports), the button should become disabled.
This PR makes it so that the button becomes enabled and disabled as the keypool state changes. The check for whether to enable or disable the receive button has changed to checking whether it is possible to get new keys. It now checks for whether the wallet has an HD seed and, if not, whether the private keys are disabled. When an action happens which would make it possible for a new address to be retrieved or make it possible for a no more addresses to be retrieved, a signal is emitted which has the GUI recheck the conditions for the Receive button. These actions are setting a new HD seed, topping up the keypool, retrieving a key from the keypool, and returning a key to the keypool.
Tree-SHA512: eff15a5337f4c64ecd7169414fb47053c04f6a0f0130341b6dd9799ac4d79f451e25284701c668971fca33f0909d5352a474a2c12349375bedfdb59b63077d50
This commit adds wallet-tool, a tool for creating and interacting with
wallet files. Original implementation was by Jonas Schnelli
<dev@jonasschnelli.ch> with modifications by John Newbery
<john@johnnewbery.com>
MSVC files were provided by Chun Kuan Lee <ken2812221@gmail.com>:
build: Add MSVC project files for bitcoin-wallet-tool
2ca632e5b4 test: Build fuzz targets into seperate executables (MarcoFalke)
fab4bed68a [test] fuzz: make test_one_input return void (MarcoFalke)
Pull request description:
Currently our fuzzer is a single binary that decides on the first few bits of the buffer what target to pick. This is ineffective as the fuzzer needs to "learn" how the fuzz targets are organized and could get easily confused. Not to mention that the (seed) corpus can not be categorized by target, since targets might "leak" into each other. Also the corpus would potentially become invalid if we ever wanted to remove a target...
Solve that by building each fuzz target into their own executable.
Tree-SHA512: a874febc85a3c5e6729199542b65cad10640553fba6f663600c827fe144543744dd0f844fb62b4c95c6a04c670bfce32cdff3d5f26de2dfc25f10b258eda18ab
6f6514a080 Correct units for "-dbcache" and "-prune" (Hennadii Stepanov)
Pull request description:
Actually, all `dbcache`-related values in the code are measured in MiB (not in megabytes, MB) or in bytes (e.g., `nTotalCache`).
See: https://github.com/bitcoin/bitcoin/blob/master/src/txdb.hba8c8b2227/src/init.cpp (L1405-L1424)
Also, "-prune" is fixed:
1. The GUI values in GB are translated to the node values in MiB correctly.
2. The maximum of the "prune" `QSpinBox` is not limited by default value of 99 (GB).
Fix: #15106
Tree-SHA512: 151ec43b31b1074db8b345fedb1dcc10bde225899a5296bfc183f57e1553d13ac27db8db100226646769ad03c9fcab29d88763065a471757c6c41ac51108459d
fa5e6ef55c wallet: Fixup rescanblockchain result doc (MarcoFalke)
Pull request description:
This was probably accidentally added to the wrong line when addressing the feedback here: https://github.com/bitcoin/bitcoin/pull/7061#discussion_r142199778
I already added the default values in #14877, but it could be clarified more that this really has no specific block height as default value, since the tip can change during a rescan.
Tree-SHA512: 48a3c5143e2b7129ee8f396d2e77550cb393fbe45f5936aeebeb7a201d61560336a3ae47b26bb757a4dbbe217e06abfd67a5a673aef266b6c4d7a80d049a2b49
04da9f4834 [RPC] Update getrawtransaction interface (Amiti Uttarwar)
Pull request description:
- stop checking unspent UTXOs for a transaction when txindex is not enabled, as per conversation here: https://github.com/bitcoin/bitcoin/issues/3220#issuecomment-377458383
- code contributed by sipa
Tree-SHA512: aa07353bccc14b81b7803992a25d076d6bc06d15ec7c1b85828dc10aea7e0498d9b49f71783e352ab8a14b0bb2010cfb7835de3dfd1bc6f2323f460449348e66
All dbcache-related values in the code are measured in MiB (not in
megabytes, MB) or in bytes.
The GUI "-prune" values in GB are translated to the node values in MiB
correctly. The maximum of the "-prune" QSpinBox is not limited by the
default value of 99 (GB).
Also, this improves log readability.
44de1561a Remove remaining chainActive references from CWallet (Russell Yanofsky)
db21f0264 Convert CWallet::ScanForWalletTransactions and SyncTransaction to the new Chain apis (Russell Yanofsky)
2ffb07929 Add findFork and findBlock to the Chain interface (Russell Yanofsky)
d93c4c1d6 Add time methods to the Chain interface (Russell Yanofsky)
700c42b85 Add height, depth, and hash methods to the Chain interface (Russell Yanofsky)
Pull request description:
This change removes uses of `chainActive` and `mapBlockIndex` globals in wallet code. It is a refactoring change which does not affect external behavior.
This is the next step in the larger #10973 refactoring change, which removes all other accesses to node global variables from wallet code. Doing this is useful to provide a better defined interface between the wallet and node, and necessary to allow wallet and node code to run in separate processes in #10102.
Tree-SHA512: 4dcec8a31c458f54e2ea6ecf01e430469b0994c5b41a21a2d150efa67cd209f4c93ae210a101e064b3a87c52c6edfc70b070e979992be0e3a00fd425de6230a8
0297be61a Allow connections from misbehavior banned peers. (Gregory Maxwell)
Pull request description:
This allows incoming connections from peers which are only banned
due to an automatic misbehavior ban if doing so won't fill inbound.
These peers are preferred for eviction when inbound fills, but may
still be kept if they fall into the protected classes. This
eviction preference lasts the entire life of the connection even
if the ban expires.
If they misbehave again they'll still get disconnected.
The main purpose of banning on misbehavior is to prevent our
connections from being wasted on unhelpful peers such as ones
running incompatible consensus rules. For inbound peers this
can be better accomplished with eviction preferences.
A secondary purpose was to reduce resource waste from repeated
abuse but virtually any attacker can get a nearly unlimited
supply of addresses, so disconnection is about the best we can
do.
This can reduce the potential from negative impact due to incorrect misbehaviour bans.
Tree-SHA512: 03bc8ec8bae365cc437daf70000c8f2edc512e37db821bc4e0fafa6cf56cc185e9ab40453aa02445f48d6a2e3e7268767ca2017655aca5383108416f1e2cf20f
faa1522e5e RPCHelpMan: Pass through Result and Examples (MarcoFalke)
Pull request description:
Passing the rpc result and rpc examples through `RPCHelpMan` makes it clear in what order they appear in the stringified version. Future improvements could then autoformat or autogenerate them.
Tree-SHA512: b32a5c178cc80f50a7e9b93a38e2b26d5994188ecafe9e61bbc599941b44b9b0e4e4be6413d4464fac6e8e73661a191a77d34917f2e6293de19fb59519dd4487
fa5f890aeb rpc: Compile on GCC4.8 (MarcoFalke)
Pull request description:
GCC 4.8 is lacking some C++11 signatures (see "Adjust C++11 signatures to take a const_iterator." in GCC 4.9: 3d2b2f494d)
Fix that by changing the code to use the pre-GCC 4.9 signature.
Can be reverted after #13356.
Fixes#15172 (reports on `Linux Mint 17.3 Rosa` and `CentOS Linux release 7.5.1804 (Core)`)
Tree-SHA512: 0c0b18968270ad4fcd0c2000c57485be881a461135dac3ad0bdab22c1a2292cf6b28ebeb930ccaa0290ff20ce87547fd07ab8189c4c4fb54d652a3d0bc9615f8
b09dab0f2d Prevent mutex lock fail even if --enable-debug (Akio Nakamura)
Pull request description:
This PR intends to resolve#15227.
```configure --enable-debug``` enables ```#ifdef DEBUG_LOCKORDER```.
Then ```lockdata``` (in sync.cpp) will be initialized same as other static objects.
But unfortunately, ```lockdata.push_lock()``` was called before its initialization (via initializing ```signatureCache``` which is declared in ```script/sigcache.cpp```) on macOS.
This PR apply the "Construct On First Use Idiom" to ```lockdata``` to prevent it.
edited --- fix typo.
Tree-SHA512: 59df99ef78a335b1b7ebed7207d4719ea4412900eea38739f6e8eaaba1f594e1950044851659ce83f4f69813fc96978244bd176676e1aa2277c813ede832e6fb
This PR intends to resolve#15227.
"configure --debug-enabled" enables "#ifdef DEBUG_LOCKORDER".
Then "lockdata" (in sync.cpp) will be initialized same as other
static objects.
But unfortunately, lockdata.push_lock() was called before its
initialization (via initializing signatureCache which is declared
in script/sigcache.cpp) on macOS.
This PR apply the "Construct On First Use Idiom" to "lockdata"
to prevent it.
a36d97d866 Default -whitelistforcerelay to off (Suhas Daftuar)
Pull request description:
No one seems to use this "feature", and at any rate the behavior of relaying transactions when they violate local policy is error-prone, if we ever consider changing the ban behavior of our software from one version to the next.
Defaulting this to off means that users who use -whitelist won't be unexpectedly surprised by this interaction. If anyone is still relying on this feature, it can still be explicitly turned on.
Tree-SHA512: 52650ad464a728d1648f496751e3f713077ea3a1de7278ed03531b2e8723e63cf2f6f41b56c98c0f73ffa22c36e01d9170b409ab452c737aca35b7ecd7a6b448
Whenever the keypool changes (new keys generated, new seed set,
keypool runs out, etc.), notify the GUI that the keypool has changed. The
receive button can then be enabled and disabled as necessary.
42ff30ec6 [Docs] add short documentation for /rest/blockhashbyheight (Jonas Schnelli)
579d418f7 [QA] add rest tests for /rest/blockhashbyheight/<HEIGHT>.<FORMAT> (Jonas Schnelli)
eb9ef04c4 REST: add "blockhashbyheight" call, fetch blockhash by height (Jonas Schnelli)
Pull request description:
Completes the REST interface for trivial block exploring by adding a call that allows to fetch the blockhash in the main chain by a given height.
Tree-SHA512: 94be9e56718f857279b11cc16dfa8d04f3b5a762e87ae54281b4d87247c71c844895f4944d5a47f09056bf851f4c4761ac4fbdbaaee957265d14de5c1c73e8d2
da6011826a Fix macOS launch-at-startup memory issue (Jonas Schnelli)
516437a1b7 Qt: remove macOS launch-at-startup option when compiled with > macOS 10.11 (Jonas Schnelli)
Pull request description:
The launch-at-startup API Bitcoin Core uses on macOS where removed in macOS 10.11 leading to a segmentation-fault due to the weak-linking when not actively compiled against SDK 10.11 (`-mmacosx-version-min=10.11`)
This PR removes the launch-at-startup feature on macOS when compiled with macOS min version > 10.11 (the default is always the macOS version you compile on).
**The depends built binaries (Gitian) are not affected since we are building with min macOS 10.10.**
Users self compiling on macOS > 10.11 can re-enable the feature by compiling with min version <= 10.11 (`CXXFLAGS="-mmacosx-version-min=10.11" CFLAGS="-mmacosx-version-min=10.11" ./configure`)
**Isn't there a new API from Apple?**
Yes, [there is](https://developer.apple.com/library/archive/documentation/MacOSX/Conceptual/BPSystemStartup/Chapters/CreatingLoginItems.html).
It will require to create a helper application which needs to be embedded in the .app folder (needs code signing as well). Developers willing to go down that rabbit hole are welcome.
Fixes#15142
Tree-SHA512: fa9cc4e39d5a2d2559919b7e22b7766f5e0269a361719294d4a4a2df2fd9d955e5b23b5907e68023fdeee297f652f844f3c447904bf18f9c1145348ad101c432
This allows incoming connections from peers which are only banned
due to an automatic misbehavior ban if doing so won't fill inbound.
These peers are preferred for eviction when inbound fills, but may
still be kept if they fall into the protected classes. This
eviction preference lasts the entire life of the connection even
if the ban expires.
If they misbehave again they'll still get disconnected.
The main purpose of banning on misbehavior is to prevent our
connections from being wasted on unhelpful peers such as ones
running incompatible consensus rules. For inbound peers this
can be better accomplished with eviction preferences.
A secondary purpose was to reduce resource waste from repeated
abuse but virtually any attacker can get a nearly unlimited
supply of addresses, so disconnection is about the best we can
do.
b301950df3 Made expicit constructor CTransaction(const CMutableTransaction &tx). (lucash-dev)
faf29dd019 Minimal changes to comply with explicit CMutableTransaction -> CTranaction conversion. (lucash-dev)
Pull request description:
This PR is re-submission of #14156, which was automatically closed by github (glitch?)
Original description:
This PR makes explicit the now implicit conversion constructor `CTransaction(const CMutableTransaction&)` in `transaction.h`.
Minimal changes were made elsewhere to make the code compilable. I'll follow up with other PRs to address individually refactoring functions that should have a `CMutableTransaction` version, or where a `CTransaction` should be reused.
The rationale for this change is:
- Conversion constructors should not be explicit unless there's a strong reason for it (in the opinion of, for example, https://google.github.io/styleguide/cppguide.html, and https://isocpp.github.io/CppCoreGuidelines/CppCoreGuidelines#Ro-conversion. Let me know your take on this).
- This particular conversion is very costly -- it implies a serialization plus hash of the transaction.
- Even though `CTransaction` and `CMutableTransaction` represent the same data, they have very different use cases and performance properties.
- Making it explicit allows for easier reasoning of performance trade-offs.
- There has been previous performance issues caused by unneeded use of this implicit conversion.
- This PR creates a map for places to look for possible refactoring and performance gains (this benefit still holds if the PR is not merged).
Tree-SHA512: 2427462e7211b5ffc7299dae17339d27f8c43266e0895690fda49a83c72751bd2489d4471b3993075a18f3fef25d741243e5010b2f49aeef4a9688b30b6d0631
223de8d94d Document RNG design in random.h (Pieter Wuille)
f2e60ca985 Use secure allocator for RNG state (Pieter Wuille)
cddb31bb0a Encapsulate RNGState better (Pieter Wuille)
152146e782 DRY: Implement GetRand using FastRandomContext::randrange (Pieter Wuille)
a1f252eda8 Sprinkle some sweet noexcepts over the RNG code (Pieter Wuille)
4ea8e50837 Remove hwrand_initialized. (Pieter Wuille)
9d7032e4f0 Switch all RNG code to the built-in PRNG. (Pieter Wuille)
16e40a8b56 Integrate util/system's CInit into RNGState (Pieter Wuille)
2ccc3d3aa3 Abstract out seeding/extracting entropy into RNGState::MixExtract (Pieter Wuille)
aae8b9bf0f Add thread safety annotations to RNG state (Pieter Wuille)
d3f54d1c82 Rename some hardware RNG related functions (Pieter Wuille)
05fde14e3a Automatically initialize RNG on first use. (Pieter Wuille)
2d1cc50939 Don't log RandAddSeedPerfmon details (Pieter Wuille)
6a57ca91da Use FRC::randbytes instead of reading >32 bytes from RNG (Pieter Wuille)
Pull request description:
This does not remove OpenSSL, but makes our own PRNG the 'main' one; for GetStrongRandBytes, the OpenSSL RNG is still used (indirectly, by feeding its output into our PRNG state).
It includes a few policy changes (regarding what entropy is seeded when).
Before this PR:
* GetRand*:
* OpenSSL
* GetStrongRand*:
* CPU cycle counter
* Perfmon data (on Windows, once 10 min)
* /dev/urandom (or equivalent)
* rdrand (if available)
* From scheduler when idle:
* CPU cycle counter before and after 1ms sleep
* At startup:
* CPU cycle counter before and after 1ms sleep
After this PR:
* GetRand*:
* Stack pointer (which indirectly identifies thread and some call stack information)
* rdrand (if available)
* CPU cycle counter
* GetStrongRand*:
* Stack pointer (which indirectly identifies thread and some call stack information)
* rdrand (if available)
* CPU cycle counter
* /dev/urandom (or equivalent)
* OpenSSL
* CPU cycle counter again
* From scheduler when idle:
* Stack pointer (which indirectly identifies thread and some call stack information)
* rdrand (if available)
* CPU cycle counter before and after 1ms sleep
* Perfmon data (on Windows, once every 10 min)
* At startup:
* Stack pointer (which indirectly identifies thread and some call stack information)
* rdrand (if available)
* CPU cycle counter
* /dev/urandom (or equivalent)
* OpenSSL
* CPU cycle counter again
* Perfmon data (on Windows, once every 10 min)
The interface of random.h is also simplified, and documentation is added.
This implements most of #14623.
Tree-SHA512: 0120e19bd4ce80a509b5c180a4f29497d299ce8242e25755880851344b825bc2d64a222bc245e659562fb5463fb7c70fbfcf003616be4dc59d0ed6534f93dd20
de7266fc3c [net] add dnsseed.emzy.de to DNS seeds (Stephan Oeste)
Pull request description:
ACK https://github.com/bitcoin/bitcoin/blob/master/doc/dnsseed-policy.md
I'm willing to keep it up and running, unless something bad happens.
I have 15+ years experience running dns servers.
About my setup:
- the server may change over time, but the service will be up all the time
- running [sipa/bitcoin-seeder](https://github.com/sipa/bitcoin-seeder) with default settings (and the non-root port redirect)
Tree-SHA512: 7abc975c148cc738d045c79d5bdb8d9926da41bb8dde66c21e954652b3c72a7aa2526af0c3c4fb8c234d3deaed5563542defe8a5137188d65ad7201b6b1d80eb
18185b57c3 scripted-diff: batch-recase BanMan variables (Carl Dong)
c2e04d37f3 banman: Add, use CBanEntry ctor that takes ban reason (Carl Dong)
1ffa4ce27d banman: reformulate nBanUtil calculation (Carl Dong)
daae598feb banman: add thread annotations and mark members const where possible (Cory Fields)
84fc3fbd03 scripted-diff: batch-rename BanMan members (Cory Fields)
af3503d903 net: move BanMan to its own files (Cory Fields)
d0469b2e93 banman: pass in default ban time as a parameter (Cory Fields)
2e56702ece banman: pass the banfile path in (Cory Fields)
4c0d961eb0 banman: create and split out banman (Cory Fields)
83c1ea2e5e net: split up addresses/ban dumps in preparation for moving them (Cory Fields)
136bd7926c tests: remove member connman/peerLogic in TestingSetup (Cory Fields)
7cc2b9f678 net: Break disconnecting out of Ban() (Cory Fields)
Pull request description:
**Old English à la Beowulf**
```
Banman wæs bréme --blaéd wíde sprang--
Connmanes eafera Coreum in.
aéglaéca léodum forstandan
Swá bealdode bearn Connmanes
guma gúðum cúð gódum daédum·
dréah æfter dóme· nealles druncne slóg
```
**Modern English Translation**
```
Banman was famed --his renown spread wide--
Conman's hier, in Core-land.
against the evil creature defend the people
Thus he was bold, the son of Connman
man famed in war, for good deeds;
he led his life for glory, never, having drunk, slew
```
--
With @theuni's blessing, here is Banman, rebased. Original PR: https://github.com/bitcoin/bitcoin/pull/11457
--
Followup PRs:
1. Give `CNode` a `Disconnect` method ([source](https://github.com/bitcoin/bitcoin/pull/14605#discussion_r248065847))
2. Add a comment to `std::atomic_bool fDisconnect` in `net.h` that setting this to true will cause the node to be disconnected the next time `DisconnectNodes()` runs ([source](https://github.com/bitcoin/bitcoin/pull/14605#discussion_r248384309))
Tree-SHA512: 9c207edbf577415c22c9811113e393322d936a843d4ff265186728152a67c057779ac4d4f27b895de9729f7a53e870f828b9ebc8bcdab757520c2aebe1e9be35
85f0ca95f3 Remove errant past from walletcreatefundedpsbt for nLocktime replaceability (Gregory Sanders)
Pull request description:
nLockTime has no bearing on bip125
Tree-SHA512: cb123242ee7e1eeff10dbfcab8e57f9aa88590e2da6794343a90a18472a97f23ce7c6bbc55b88163e007fe38c5d8ee5b749cc4ce2bf145f560e084d61b568159
1ed425ea17 gui: Fix window title update (João Barbosa)
Pull request description:
Removes trailing `-` from window title when running on mainnet.
Reported by @Sjors in https://github.com/bitcoin/bitcoin/pull/15149#issuecomment-455787938.
Tree-SHA512: 22f13c361496720f30a4926d928851ed74456c0d70bd313b0ebaca91a9ebfde96991091ac3d1b094f33d3ce9afafd709eb1917f00d96fa3ca69751b6b14e1d2b
a2a6c8f453 rpc: remove duplicate solvable field from getaddressinfo (fanquake)
Pull request description:
Also added optional to `iscompressed`.
Tree-SHA512: 28442a9dbfb2a9992b9b57142fa13d374d39444f04ae63460cb6330d896160cfd4b9651a3e231893eac3142ce55eff597a54cbafd3b57ffa46d3711c64044acb
0dd9bdefa gui: Refactor to use WalletController (João Barbosa)
8fa271f08 gui: Add WalletController (João Barbosa)
cefb399e2 gui: Use AutoConnection for WalletModel::unload signal (João Barbosa)
Pull request description:
This PR is a subset of the work done in the context of #13100. This change consists in extracting from the application class the code that manages the wallet models.
The role of the `WalletController` instance is to coordinate wallet operations and the window.
Tree-SHA512: 6a824054376730eb7d16c643dd2003f5f60778e8ad3af707b82bc12c48438db179ca4446316b28fb17b206f4b9aba8998419aab8c5dd1f7c32467015732b5094
24313fbf7e Remove redundant stopExecutor() signal (Hennadii Stepanov)
1c0e0a5e38 Remove redundant stopThread() signal (Hennadii Stepanov)
Pull request description:
The `QThread::finished` signal do this work.
Tree-SHA512: 1afce23d30232276d50c3af5af79d83b88e390a2b71f7df585cc1079585d330447d179bbc34c0a89599beb2da035dfd5b9ce23238171490825cabc3a19ae6e67
It includes the following policy changes:
* All GetRand* functions seed the stack pointer and rdrand result
(in addition to the performance counter)
* The periodic entropy added by the idle scheduler now seeds stack pointer,
rdrand and perfmon data (once every 10 minutes) in addition to
just a sleep timing.
* The entropy added when calling GetStrongRandBytes no longer includes
the once-per-10-minutes perfmon data on windows (it is moved to the
idle scheduler instead, where latency matters less).
Other changes:
* OpenSSL is no longer seeded directly anywhere. Instead, any generated
randomness through our own RNG is fed back to OpenSSL (after an
additional hashing step to prevent leaking our RNG state).
* Seeding that was previously done directly in RandAddSeedSleep is now
moved to SeedSleep(), which is indirectly invoked through ProcRand
from RandAddSeedSleep.
* Seeding that was previously done directly in GetStrongRandBytes()
is now moved to SeedSlow(), which is indirectly invoked through
ProcRand from GetStrongRandBytes().
This guarantees that OpenSSL is initialized properly whenever randomness
is used, even when that randomness is invoked from global constructors.
Note that this patch uses Mutex directly, rather than CCriticalSection.
This is because the lock-detection code is not necessarily initialized
during global constructors.
89282379ba threads: fix unitialized members in sched_param (Cory Fields)
Pull request description:
Rebased theuni's #14342.
Building with gcc 8.2 against musl libc, which apparently has more attributes available in its sched_param. The following warnings were produced:
warning: missing initializer for member 'sched_param::sched_ss_low_priority' [-Wmissing-field-initializers]
warning: missing initializer for member 'sched_param::sched_ss_repl_period' [-Wmissing-field-initializers]
warning: missing initializer for member 'sched_param::sched_ss_init_budget' [-Wmissing-field-initializers]
warning: missing initializer for member 'sched_param::sched_ss_max_repl' [-Wmissing-field-initializers]
Since the current thread may have interesting non-zero values for these fields, we want to be sure to only change the intended one. Query and modify the current sched_param rather than starting from a zeroed one.
Tree-SHA512: a0bedbcf0130b3ee8261bb704e4bf6c9b760ad377c8a28c258765d54e54462b76707efc188b936b0a635cdd2bdf6b3b9298ab06ba361dc4806150b670d9702a3
These are separate events which need to be carried out by separate subsystems.
This also cleans up some whitespace and tabs in qt to avoid getting flagged by
the linter.
Current behavior is preserved.
b745e149c2 [docs] Expand help text for importmulti changes (John Newbery)
Pull request description:
Expands the RPC help text for changes to the importmulti RPC method.
Tree-SHA512: e90e5abf66bba3863e7519b5f79c26d18a4d624e6e7878293bdd4ebb57f1a01c67de52e4a5621901a8cb87fb3516264b3b1a826997c7c3c17b11216f1f1a3db0
4a86a0acd9 Make SafeDbt DB_DBT_MALLOC on default initialization (Ben Woosley)
1a9f9f7e5e Introduce SafeDbt to handle DB_DBT_MALLOC raii-style (Ben Woosley)
951a44e9cd Drop unused setRange arg to BerkeleyBatch::ReadAtCursor (Ben Woosley)
Pull request description:
This provides additional exception-safety and case handling for the proper
freeing of the associated buffers.
Tree-SHA512: a038d728290cdb3905e7d881608052a6675b6425729ceaf7cfe69a6e91c2ee293cdb01e4b695a20963459ffdd9d4a1f9a08b3c07b1b5ba1aa8590a8149f686db
b9dafe7d9f Fix remaining compiler warnings (MSVC). Move disabling of specific warnings from /nowarn to project file. (practicalswift)
Pull request description:
Fix remaining compiler warnings (MSVC).
Before:
```
$ msbuild /p:TrackFileAccess=false /p:CLToolExe=clcache.exe build_msvc\bitcoin.sln /m /v:q /nowarn:C4244;C4267;C4715 /nologo
…\script\script.cpp(272): warning C4018: '>': signed/unsigned mismatch
…\test\allocator_tests.cpp(147): warning C4312: 'reinterpret_cast': conversion from 'int' to 'void *' of greater size
…\boost\test\tools\old\impl.hpp(107): warning C4805: '==': unsafe mix of type 'const Left' and type 'const Right' in operation
…\test\crypto_tests.cpp(535): warning C4334: '<<': result of 32-bit shift implicitly converted to 64 bits (was 64-bit shift intended?)
…\test\script_tests.cpp(188): warning C4805: '==': unsafe mix of type 'int' and type 'bool' in operation
…\test\script_tests.cpp(190): warning C4805: '==': unsafe mix of type 'int' and type 'bool' in operation
…\test\script_tests.cpp(191): warning C4805: '==': unsafe mix of type 'int' and type 'bool' in operation
$
```
After:
```
$ msbuild /p:TrackFileAccess=false /p:CLToolExe=clcache.exe build_msvc\bitcoin.sln /m /v:q /nowarn:C4244;C4267;C4715;C4805 /nologo
$
```
Tree-SHA512: 5b30334d3804e869779e77dad75a799e8e5e7eb2e08634cd40035cce140edd623cbb6c8b5806d2158c3df97888d3ea9ff4b8b6a5a83de3fe2cb361e29588c115
e4a0c3547e Improve blocksdir functional test. (Hennadii Stepanov)
c3f1821ac7 Make blockdir always net specific (Hennadii Stepanov)
Pull request description:
The blocks directory is net specific by definition.
Also this prevents the side effect of calling `GetBlocksDir(false)` in the non-mainnet environment.
Currently a new node creates an unused `blocks\` directory in the root of the data directory when `-testnet` or `-regtest` is specified.
Refs:
- #12653
- https://github.com/bitcoin/bitcoin/pull/12653#discussion_r174784834 by @laanwj
- https://github.com/bitcoin/bitcoin/issues/14595#issuecomment-436011186
Tree-SHA512: c9957a68a4a200ebd2010823a56db7e61563afedcb7c9828e86b13f3af2990e07854b622c1f3374756f94574acb3ea32de7d2a399eef6c0623f0e11265155627
Added a note that results can be queried in the parenthesized syntax.
Deprecated boolean `verbose` replaced with numerical `verbosity` in
`getblock` examples.
fe7048b39 gui: Show current wallet name in window title (João Barbosa)
8a7926112 gui: Keep network style in BitcoinGUI (João Barbosa)
f411c8b35 gui: Remove unused return type in some BitcoinGUI methods (João Barbosa)
Pull request description:
<img width="876" alt="screenshot 2019-01-11 at 23 58 26" src="https://user-images.githubusercontent.com/3534524/51065458-d7ebaf80-15fc-11e9-9162-e37e9a10d448.png">
Tree-SHA512: 5c43f615834983bc1c5045e07c6e119044dd78ca947fd2679d302b519d5ce1d08d29ca00b1c11e88c4bbc4d56f2e6f4a8adc42084f3503e751e642e8a13112dc
fa5e373365 validation: Add cs_main locking annotations (MarcoFalke)
fa5c346c5a doc: Add comment to cs_main and mempool::cs (MarcoFalke)
fafe941bdd test: Add missing validation locks (MarcoFalke)
fac4558462 sync: Add RecursiveMutex type alias (MarcoFalke)
Pull request description:
Both the chain state and the transaction pool are validation specific, but access to them is protected by two locks. The two locks have the following semantics:
* Writing to the chain state or adding transactions to the transaction pool -> Take both `cs_main` and `mempool::cs`
* Reading either or removing transactions from the the transaction pool -> Take only the appropriate lock
Tree-SHA512: 6f6e612ffc391904c6434a79a4f3f8de1b928bf0a3e3434b73561037b395e2b40a70a5a4bd8472dd230e9eacc8e5d5374c904a3c509910cf3971dd7ff59a626c
Only change in behavior is "Rescan started from block <height>" message
replaced by "Rescan started from block <hash>" message in
ScanForWalletTransactions.
Co-authored-by: Ben Woosley <ben.woosley@gmail.com>
And use them to remove uses of chainActive and mapBlockIndex in wallet code
This commit does not change behavior.
Co-authored-by: Ben Woosley <ben.woosley@gmail.com>
And use them to remove uses of chainActive and mapBlockIndex in wallet code
This commit does not change behavior.
Co-authored-by: Ben Woosley <ben.woosley@gmail.com>
And use them to remove uses of chainActive and mapBlockIndex in wallet code
This commit does not change behavior.
Co-authored-by: Ben Woosley <ben.woosley@gmail.com>
fb3ce75807 Don't label transactions "Open" while catching up (Hennadii Stepanov)
Pull request description:
Fix#13299.
Since the default `nSequence` is `0xFFFFFFFE` and locktime is enabled, the checking `wtx.is_final` is meaningless until the syncing has completed (ref: #1026).
This PR makes the wallet mark a transaction "Unconfirmed" instead of misleading "Open for NNN more blocks" when syncing after a period of being offline.
Before this PR (with the issue):

With this PR (the issue has been resolved):
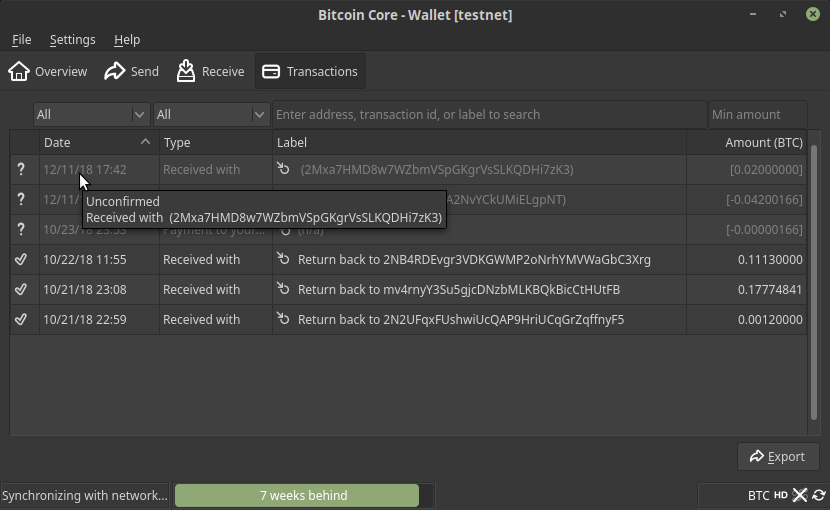
Tree-SHA512: 358ec83b43c266a4d32a37a79dda80e80d40a2b77ad38261c84a095e613399f674aa7184805b3f6310e51ddb83ae2636b8849fcc7c4333e1b3ecbb0f70ad86d3
a88640e123 Fix minimized window bug on Linux (Hennadii Stepanov)
Pull request description:
Fix#14591
On some Linux systems the minimized to the taskbar (iconified) main window cannot be restored properly using actions from the systray icon menu when `QSystemTrayIcon::contextMenu()` is a child of the main window.
Tree-SHA512: 05c9f724fc2278d45dac6fe72b09859f12b5d71f54659bb779403c8cd81b55e610fb7b5aa912ac273d3cd19bf953b0405bbc6451feb00d1827c95dd9f0876aa4
645e905c32 doc: Add release notes for unloadwallet change to synchronous call (João Barbosa)
c37851de57 rpc: Make unloadwallet wait for complete wallet unload (João Barbosa)
Pull request description:
Currently the `unloadwallet` RPC is asynchronous, it only signals the intent to unload the wallet and then returns the response to the client. The actual unload can happen later and the client has no way to be notified of that.
This PR makes the `unloadwallet` RPC synchronous, meaning that it blocks until the wallet is fully unloaded.
Replaces #14919, fixes#14917.
Tree-SHA512: ad88b980e2f3652809a58f904afbfe020299f3aa6a517f495ba943b8d54d4520f6e70074d6749be8f5967065c0f476e0faedcde64c8b4899e5f99c70f0fd6534
a0ac15459a doc: Add getrpcinfo release notes (João Barbosa)
251a91c1bf qa: Add tests for getrpcinfo (João Barbosa)
d0730f5ce4 rpc: Add getrpcinfo command (João Barbosa)
068a8fc05f rpc: Track active commands (João Barbosa)
bf4383277d rpc: Remove unused PreCommand signal (João Barbosa)
Pull request description:
The new `getrpcinfo` command exposes details of the RPC interface. The details can be configuration properties or runtime values/stats.
This can be particular useful to coordinate concurrent functional tests (see #14958 from where this was extracted).
Tree-SHA512: 7292cb6087f4c429973d991aa2b53ffa1327d5a213df7d6ba5fc69b01b2e1a411f6d1609fed9234896293317dab05f65064da48b8f2b4a998eba532591d31882
3a0e76fc12 Replace remaining 0 with nullptr in Qt code (Ben Woosley)
9096276e0b Don't use zero as null pointer constant (-Wzero-as-null-pointer-constant) (practicalswift)
Pull request description:
This corrects all violations of `-Wzero-as-null-pointer-constant` identified in the Qt codebase.
These changes are extracted from #15112 as suggested by @MarcoFalke to ease review. This is in service of enabling `-Wzero-as-null-pointer-constant`, which should eliminate this as a concern going forward.
Note there are 2 non-Qt changes: `src/test/allocator_tests.cpp` and `src/wallet/db.cpp`.
Tree-SHA512: 206bd668802147ba42bc413c2d7d259cb59aca9ec1da74a6bf2ca3932e60ae492faacbc61bcee0fd6b4b49a4d59d075b7e5404f0526b36c47718f9b0587e7768
fac2f5ecae Use C++11 default member initializers (MarcoFalke)
Pull request description:
The second and last change on this topic (c.f. #15109). Split up because the diff would otherwise interleave, making review harder than necessary.
This is not a stylistic change, but a change that avoids bugs such as:
* fix uninitialized read when stringifying an addrLocal #14728
* qt: Initialize members in WalletModel #12426
* net: correctly initialize nMinPingUsecTime #6636
* ...
Tree-SHA512: 547ae72b87aeaed5890eb5fdcff612bfc93354632b238d89e1e1c0487187f39609bcdc537ef21345e0aea8cfcf1ea48da432d672c5386dd87cf58742446a86b1
d6b076c17b Drop IsLimited in favor of IsReachable (Ben Woosley)
Pull request description:
These two methods have had the same meaning, but inverted, since
110b62f069. Having one name for a single
concept simplifies the code.
This is a follow-up to #15051.
/cc #7553
Tree-SHA512: 347ceb9e2a55ea06f4c01226411c7bbcade09dd82130e4c59d0824ecefd960875938022edbe5d4bfdf12b0552c9b4cb78b09a688284d707119571daf4eb371b4
There was only one place in the codebase where we're directly reading >32 bytes from
the RNG. One possibility would be to make the built-in RNG support large reads, but
using FastRandomContext lets us reuse code better.
There is no change in behavior here, because the FastRandomContext constructor
uses GetRandBytes internally.
9d0e52834 implements different disk sizes for different networks on intro (marcoagner)
Pull request description:
Fixes https://github.com/bitcoin/bitcoin/issues/13213.
Mostly, I layed out the concept to open the PR for refinement and getting feedback if the approach is okay. Changes are expected.
Two points:
- The values for both new consts `TESTNET_BLOCK_CHAIN_SIZE` and `TESTNET_CHAIN_STATE_SIZE` is certainly not optimal; I just checked the size of my testnet3 related dirs and set them to little bit higher values. Which values should be used?
- Should we do something like this to regtest? Or these "niceties" do not matter when on regtest?
Thanks!
Tree-SHA512: 8ae87a29fa8356b899e7a823c76cde793d9126b4ee59554d7a2a8edb088fe42a19976b34c06c2fd4a98a727e1e4971dd983f42b6093ea6caa255b45004e22bb4
332b3dd7c1 util: Make ToLower and ToUpper take a char (Wladimir J. van der Laan)
edb5bb3500 util: remove unused [U](BEGIN|END) macros (Wladimir J. van der Laan)
7fa238c701 Replace use of BEGIN and END macros on uint256 (Wladimir J. van der Laan)
Pull request description:
Two cleanups in `util/strencodings.h`:
- Remove `[U](BEGIN|END)` macros — The only use of these was in the Merkle tree code with `uint256` which has its own `begin` and `end` methods which are better.
- Make ToLower and ToUpper take a char — Unfortunately, `std::string` elements are (bare) chars. As these are the most likely type to be passed to these functions, make them use char instead of unsigned char. This avoids some casts.
Tree-SHA512: 96c8292e1b588d3d7fde95c2e98ad4e7eb75e7baab40a8e8e8209d4e8e7a1bd3b6846601d20976be34a9daabefc50cbc23f3b04200af17d0dfc857c4ec42aca7
fa48baf23e wallet: Avoid leaking locktime fingerprint when anti-fee-sniping (MarcoFalke)
453803adc9 [test] wallet_txn_clone: Correctly clone txin sequence (MarcoFalke)
Pull request description:
The wallet sets the locktime to the current height of our active chain. This is fine, as long as our node is connected to other nodes. However, when we fall back and get stuck at a particular height (e.g. taking the wallet offline), the same (potentially unique) locktime is used for all transactions. This makes it easier for passive observers to cluster transactions by wallet.
For reference, I visualized "locktime-reuse" with the data:
* blocks 545k-555k (both inclusive)
* locktimes<=60k
* excluding coinbase txs

Tree-SHA512: 2af259dd8f9f863312e2732d80ca8ba6a20c8d6d1c486b10a48479e1c85ccf13b0c38723740ebadde0f28d321cd9c133ad3e5d1e925472eb27681143bda2d0e7
Unfortunately, `std::string` elements are (bare) chars. As these
are the most likely type to be passed to these functions, make them use
char instead of unsigned char. This avoids some casts.